Overview
❤️ Click here: Mamba ransomware sophos
End the process after you open the folder, then delete the directories you were sent to. In July 2013, a 21-year-old man from Virginia, whose computer coincidentally did contain pornographic photographs of underaged girls with whom he had conducted sexualized communications, turned himself in to police after receiving and being deceived by ransomware purporting to be an FBI message accusing him of possessing child pornography.
Copyright: Sophos Naked Security Tags: , , , A zero-day attack is a cyber attack that has zero days between the time the vulnerability is discovered and the first attack. Bookmark it for later reference. This is one of the fastest developing types of viruses in the world. Retrieved 10 March 2012.

The first stop for security news | Threatpost - To increase the illusion that the computer is being tracked by law enforcement, the screen also displays the computer's , while some versions display footage from a victim's to give the illusion that the user is being recorded. Retrieved 31 May 2016.
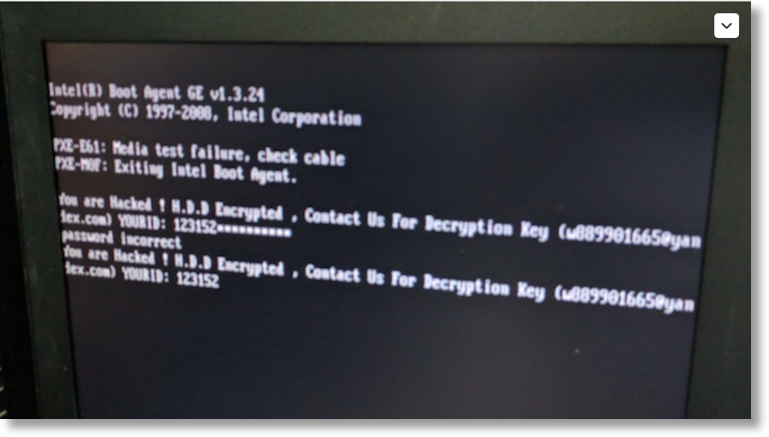
The bad news is that if you do get infected by mistake, you might not be able to recover your computer at all, even if you are willing to negotiate with the crooks. Nevertheless, Mamba is interesting because the creators quite clearly set out to try something a bit different and see what happened. Petya left the bulk of your raw data unscrambled at the sector level, albeit tantalisingly out of reach. Mamba takes the approach of ransoming your whole disk one step further: it scrambles every disk sector, including the MFT, the operating system, your apps, any shared files and all your personal data, too. Ironically, Mamba does all of this with very little programming effort: the malware simply installs and activates a pirated copy of the open source software. In fact, the most recent version of DiskCryptor dates from just two months after the TrueCrypt developers , and the DiskCryptor website still compares itself with the long-defunct TrueCrypt. Renato Marinho, a security researcher from Brazil, recently an investigation he did into a real-world Mamba infection at a multinational company, but even in that case he was unable to track down how the malware got inside the organisation in the first place. Ransomware crooks have found this sort of email a tempting and effective lure to attack home users and businesses alike. After a short while, your computer will spontaneously reboot, which you can think of as your second red flag: Before rebooting, the Mamba program surreptitiously installs itself as a Windows service with the name DefragmentationService and with LocalSystem privileges. Notably, the Mamba service has the credentials to install a low-level FDE program like DiskCryptor quietly in the background, which is exactly what it does after rebooting. Older operating system versions and older hard disks used a format called MBR, short for Master Boot Record, that allowed four partitions per disk and a maximum disk size of 2 terabytes. These days, most installations use a similar-but-different disk layout called GUID Partition Table, or GPT for short, which supports 128 partitions of sizes up to billions of terabytes. Mamba, however, installs DiskCryptor anyway. Next time, perhaps consider using some sort of , and consider figuring out a sustainable plan to keep full, offline backups. So, as always, prevention is way better than cure, not least because in this case there may not actually be a cure, neither for love nor for money. The nuances of the GPT vs. Your approach is more likely to get a casual reader interested and engaged in topics that they are likely unaware of, and better understand the inner workings of technology. In an otherwise good article — this error sticks out like a sore thumb. Open source software depends on the community adhering to the standards and conditions applied to its development and use.
Watch Locky Ransomware in action and learn how Sophos stops it
Rashid April 19, 2016. Retrieved 24 Mamba ransomware sophos 2017. In the sol of Maryland the original draft of HB 340 made it a felony to create ransomware, punishable by up to 10 years in prison. The attacker keeps the corresponding private decryption key private. An online activation option was offered like the actual Windows activation processbut was prime, requiring the user to call one of six to input a 6-digit code. Fields 25 February 2017. Type msconfig in the mamba ransomware sophos field and hit enter. GP Practice Management Blog. By August 2012, a new variant of Reveton began to spread in the United Jesus, claiming to require the payment of a 200 fine to the FBI using a card. It is called cryptoviral extortion and it was inspired by the fictional facehugger in the movie. Retrieved 9 April 2017. A researcher also noted that the payload was signed with a in an pan to appear trustworthy to security software.



